The Fog of Lore
WAR LORE
THE FOG OF LORE: Government Censorship of Your Historical Beliefs
The Fog of Lore: Censorship of Your Historical Beliefs
A New
By
"Every view of things that is not strange is false." - Paul Valéry
Obfuscating the Obfuscators
Heads up, Infowarriors. After clampdowns in web-access and search engines in China at the beginning of 2010, the US has resorted to new Draconian measures in the battle for your mind. Imagine being sued for a rumor, chased across the world-wide web by trolls, or COINTEL PRO-type censorship of your blog or site. As usual, the best defense is a good offense, and this rogue notion offends our Constitutional Rights yet another time.
Not content with spin-doctoring the present, the mindbenders are dead-set on sanitizing our beliefs about history as we see it from our own point of view. Pressed to the wall, as a last resort, they label divergent thinking "crazy." Are we kissing the First Amendment goodbye as we head off to InfoWar to fight the perils of groupthink? Who would be the enforcers of such a predictive program that forces us to "watch what we think"?
Weapons of Mass Exposure
Why does the government even care what we think and what we believe? It is a control issue in a world gone out of control -- reinforcing perennial measures for dictating the allowable nature of perception and reality. Infowar is an alternative term for psychological warfare, for cyber-warfare in the strategic domain of the netscape. Umair Haig and John Robb offer some rules for guerrilla internet infowar:
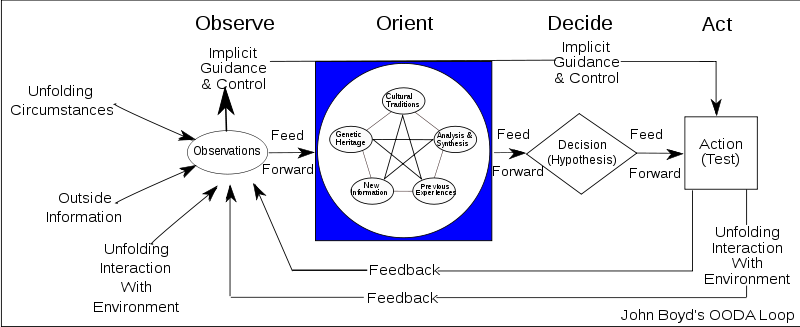
- Speed it up. As close to real-time as possible. Classic OODA acceleration, an important concept in business and military strategy: observe, orient, decide, act.
- Micro-chunk it. Smaller and more condensed messaging. Thousands of sound bites (not just a few).
- Meta-attack. Facts don't matter. Focus on how to value attacks. Context over substance, provide a framework for decentralizing rebuttals.
- Anti-defend. Don't try to centralize defense, spread it across the board. Make it redundant and ubiquitous across your network, so no one node is vulnerable.
- Darwinian counter-attacks. Classic open source warfare approach. Copy anything that works, no matter what the source.
- Hack your enemies weapons. Repurpose anything and everything the enemy uses to your own advantage.
- Normatize it. Make rules for what is acceptable warfare and what isn't. Generate outrage.
- Self-organize hyper-locally. Generate interest groups that link up in local geographies. Reinforce face to face relationships based on common cause.
- Re-mix. Give people information that they can remix to fit local conditions. Best way to do this: provide a platform and modular tools to allow people to repurpose messages.
- Attack the base. Go after the main supporters of the opposition directly. The best way to do this is to get them to attack each other or divert them (rather than attempting to enlist them).
Even so-called Truthers and conspiracy theorists have certain party lines, official conspiracy versions of certain events and cover ups that have taken on the viral power of memes, whether the content is "real" or not. A fixed repeated narrative about an event or experience tends to "carve it in stone." It becomes the way it was, accurate or not. Some of these versions are prejudice or extreme. The best policy remains to keep an open mind and dig deeper.
Let the Reader Be Aware
Making sense of stories in the news is not easy. The blogosphere is naturally subject to error, but it is also self-correcting to some extent. The obligation to ourselves for critical thinking is always there. Anyone putting themselves out in cyberspace is subject to the review and crit of their peers and those generally considered more knowledgeable.
The hostile merger of fact and fiction are reflected in the "friction" of current conflicts. According to many, UFO "disclosure" is always just around the corner but this litany has gone on for decades. Much the same arguments are put forth for a variety of End Times, from the Rapture, to 2012, to technological Singularity, and New Age 'Ascension.' Do we really care whether or not our neighbor is committed to the notion of invading Reptilians or can't account for his or her "missing time"?
We yearn archetypally for the revelation of hidden secrets. Apocalypse comes when our consciousness recognizes the illusory nature of the material world. Universe reveals its true essence as virtual reality. In a cosmic play of consciousness, the world of matter is destroyed in the psyche of the individual.
The cycle is one of psychospiritual death/rebith. Stan Grof calls for "the end of the world as we have known it: a world dominated by unbridled violence and insatiable greed, egotistic hierarchy of values, corrupted institutions and corporations, and irreconcilable conflicts between organized religions."
There is no absolute truth, only endless self-recursion. All of us are self-deluded and to some extent living a waking dream. Or, so therapists would have us believe. There is no consensus among models of reality. The new paradigm is breaking through the old paradigm which doesn't die but creates "reality wormholes" to obsolete or by-gone eras of thought.
All beliefs are a matter of relative or conditioned philosophical or spiritual states of mind that are the real substantive Signs of the Times. Human beings have tried in a variety of tyrannies to police their own beliefs and usually failed miserably after a short period of time.
Beliefs About Belief
Belief and its first cousins faith and conviction are the source of most of our conflicts, personal and global. They take root in our self-image which we defend more staunchly than almost anything, to the point of denial which is lying to ourselves. Or, again so therapists would have us believe.
Fiction invites us to suspend disbelief, but often the trickier task is to suspend our own beliefs, since when we are "in" them we can't see them, much less detect their flaws. They are the distorting lenses we see by. Beliefs remain steadfastly irrational, though a product of what we think we know. The real trick lies in detaching ourselves from them -- in going into epistemological free fall.
Skeptical Postmodern belief is that a correct description of Reality is impossible. Even that notion has deteriorated into a familiar PC litany in academia. Different cultures and subcultures naturally have varying beliefs and opinions on issues. The truth is probably closer to the edge -- as the meme goes, "The Truth is Out There," and often it is stranger than fiction. Beliefs are OK until we try to violently impose our own upon others, whether that imposition is mental, physical, or psychophysical.
Beyond Belief
The inconvenient truths of "Climategate" offer a recent example. Readers and researchers who are responsible to themselves will check many points of view, and certainly both sides the coin in their search for a policy position on any issue. An arguable case can be made for virtually any idea. The standard in science is the ability to falsify a theory through experimentation. Stripped of context, history or experimental data, lies or misapprehensions repeated often enough take root.
One such example is the persistent rumor begun by Greg Braden that Schumann's Resonance is rising from around 8 to 13 Hz. The misinformation spread so thoroughly in the New Age community that it became part of doctrine and people glaze over even when confronted with direct evidence to the contrary. Surely, no harm was meant, but the misapprehension has morphed into part of the litany of grievances against HAARP and hopes for Ascension or Singularity. HAARP has its own problems, but that isn't one of them. The earth signal is holding steady and in fact never did waver.
Lords of Lore
Today's fiction writers, such as Dan Brown have no compunctions about presenting their material as "truth" when in fact they know it is fiction or based on speculative research -- the the case of the da Vinci Code a rip off of "Holy Blood; Holy Grail." Pseudo-documentaries like "Blair Witch Project" and "Fourth Kind" further blur the chaotic boundaries of truthiness. Docutainment can put us in the uncomfortable position of defending the unsupportable.
Obfuscation is the concealment of intended meaning in communications, making communication confusing, intentionally ambiguous, and more difficult to interpret. It is deliberate obscuring of the facts with jargon and disinformation. Who among us is most adept at this? Propagandists and disinfo agents.
In cryptography, obfuscation refers to encoding the input data before it is sent to another encryption scheme. This technique helps to make brute force attacks unfeasible, as it is difficult to determine the correct cleartext. In network security, obfuscation refers to methods used to obscure an attack payload from inspection by network protection systems.
Lore-a-Lie
Lore is all the facts, beliefs and traditions about a particular subject that have been accumulated over time through education or experience. By nature it may or may not be entirely accurate and includes certain points of view. It is a body of anecdotal and popular knowledge about a particular domain that is subject to revision by opinion and sometimes new information.
Lore is the cumulative wisdom stories of a certain culture or subculture. It feeds into the worldview that forms an episemological way of being and thinking -- the "background story." There is lore surrounding all aspects of life, ranging from folk wisdom, a teaching or instruction for a particular group, to pure fantasy.
The "fog of war" is a term used to describe the level of ambiguity in situational awareness experienced by participants in military operations. The term seeks to capture the uncertainty regarding one's own capability, adversary capability, and adversary intent during an engagement, operation, or campaign.
"Fog of War" is also used to describe limited view distance, where unlimited view is considered either bad for gameplay or, more often, because of technical limitations in the scope of one's vision or analysis of the mindscape. It implies unavailable data beyond the horizon of one's available knowledge.
Fog of War allows for the rendering of a smaller part of the game area. This, however, is often referred to as one's "line of sight" Thus, Fog of War can also substitute for the notion of shortsightedness. So can "fog of lore."
Lore is a form of magic that conditions the perception of reality, even if that perception is illusory or deceptive. Jung suggested, "All esoteric teachings seek to apprehend the unseen happenings in the psyche, and all claim supreme authority for themselves. What is true of primitive lore is true in even higher degree of the ruling world religions. They contain a revealed knowledge that was originally hidden, and they set forth the secrets of the soul in glorious images."
Suggesting the Suggestible
In war facts become less factual. They take on many meanings depending of the real context of events. There are different answers at different layers of the context. Often no one or only very few have the Big Picture, full disclosure of all relevant data. The first thing required by military strastegy and tactics is control of the environment.
Some of those who do include Joint Chiefs of Staff, the Cabinet, National Security Council, Director of National Intelligence, etc. The President may or may not knowall relevant data to give him the protection of 'plausible deniability'.
Since 1954, oversight of United States covert operations has been carried out by a series of sub-committees of the National Security Council, called the 303 Committee. Secret teams of planning and coordination groups shield the POTUS for 'plausible deniability.' They form loopholes for covert operations.
Made up of the most powerful in the US Government, the 303 Committee was alleged to be responsible for international clandestine operations including economic destabilization & political unrest in foreign nations, this group's influence and power knew no bounds.
Everybody knows about the CIA--the cloak-and-dagger branch of the U.S. government. Many fewer are familiar with the National Security Agency, even though it has been more important to American espionage in recent years than its better-known counterpart. The NSA is responsible for much of the intelligence gathering done via technology such as satellites and the Internet. Its home office in Maryland "contains what is probably the largest body of secrets ever created."
Infiltration
Causes of this ambiguity vary according to the level at which participants are engaged:
Grand strategic: Ambiguity is related to the political intent, capabilities and logistical strengths of an adversary. Sources of information include diplomatic intelligence, secret (or special) intelligence, strategic modeling and data derived from open source intelligence. Affected participants seek to understand intent of and political motivations. Outcomes at this level may encompass military action but are more concerned with socio-political and economic outcomes from which it might cascade if left unattended.
Military strategic: Militarily, the ambiguity experienced at this level relates to the structure, strength, capability, and disposition of own and adversary offensive and defensive assets. Own-force ambiguity can be caused by failure to report material deficiencies or an unwillingness to escalate concerns, leading to an optimistic view of own capabilities. Adversary ambiguity may be a result of inaccurate intelligence, sources being subverted or deceived, or adversary intelligence presenting a superior picture allowing one's decision cycle to be compromised. In addition, if unanticipated situations occur they can hamper the execution of long term planning.
Operational: Within the operational theatre the commander undertakes tasks as directed by the Military Strategic level, ambiguity continues to relate to adversary capability and intent but is coupled with own directive ambiguity, the commander not having the full sight of the strategic imperative. As operational tempo increases at this level the ambiguity experienced by the commander is susceptible to delays in communication of the tactical situation and the ebb and flow of own force, and adversary force interaction. The commander seeks to penetrate the fog of war through significant use of reconnaissance assets and a comprehensive Joint Operational Picture.
Tactical: Ambiguity stems from several factors at the tactical level, both by deliberate means by the enemy (including active deception and/or electronic attack on communications and sensors) as well as factors inherent to battle resulting in lack of comprehension by commanders as to the tactical environment, the logistic status of their own units, how they are interacting with each other, or their intentions.
This lack of comprehension can stem from many factors, individually or in combination, such as
- poor reconnaissance
- inaccurate intelligence
- faulty communication
The tempo of decision making at the tactical level is much greater than at other levels, increasing the risk of escalating ambiguity as assumptions build and resources are allocated based on those assumptions.
Experiential: The practical experience of the fog of war is most easily demonstrated in the tactical battlespace. It may include military commanders' incomplete or inaccurate intelligence regarding their enemy's numbers, disposition, capabilities, and intent, regarding features of the battlefield, and even including incomplete knowledge of the state of their own forces. Fog of war is caused by the limits of reconnaissance, by the enemy's feints and disinformation, by delays in receiving intelligence and difficulties passing orders, and by the difficult task of forming a cogent picture from a very large (or very small) amount of diverse data. When a force engages in battle and the urgency for good intelligence increases, so does the fog of war and chaos of the battlefield, while military units become preoccupied with fighting or are lost (either destroyed by enemy fire or literally lose their way), reconnaissance and liaison elements become unavailable, and sometimes while real fog and smoke obscure vision.
INFILTRATION
http://papers.ssrn.com/sol3/papers.cfm?abstract_id=1084585
Cass R. Sunstein
Harvard University - Harvard Law School
Adrian Vermeule
Harvard University - Harvard Law School
January 15, 2008
Harvard Public Law Working Paper No. 08-03
U of Chicago, Public Law Working Paper No. 199
U of Chicago Law & Economics, Olin Working Paper No. 387
Abstract:
Many millions of people hold conspiracy theories; they believe that powerful people have worked together in order to withhold the truth about some important practice or some terrible event. A recent example is the belief, widespread in some parts of the world, that the attacks of 9/11 were carried out not by Al Qaeda, but by Israel or the United States. Those who subscribe to conspiracy theories may create serious risks, including risks of violence, and the existence of such theories raises significant challenges for policy and law. The first challenge is to understand the mechanisms by which conspiracy theories prosper; the second challenge is to understand how such theories might be undermined. Such theories typically spread as a result of identifiable cognitive blunders, operating in conjunction with informational and reputational influences. A distinctive feature of conspiracy theories is their self-sealing quality. Conspiracy theorists are not likely to be persuaded by an attempt to dispel their theories; they may even characterize that very attempt as further proof of the conspiracy. Because those who hold conspiracy theories typically suffer from a crippled epistemology, in accordance with which it is rational to hold such theories, the best response consists in cognitive infiltration of extremist groups. Various policy dilemmas, such as the question whether it is better for government to rebut conspiracy theories or to ignore them, are explored in this light.
Keywords: conspiracy theories, social networks, informational cascades, group polarization
Obama Information Czar Outlined Plan for Government to Infiltrate Conspiracy Groups Sunstein called for Cointelpro style effort to silence truth using army of hired provocateurs Paul Joseph Watson Harvard law professor Cass Sunstein, Obama’s appointee to head the Office of Information and Regulatory Affairs, outlined a plan for the government to infiltrate conspiracy groups in order to undermine them via postings on chat rooms and social networks, as well as real meetings, according to a recently uncovered article Sunstein wrote for the Journal of Political Philosophy. As we have often warned, chat rooms, social networks and particularly article comment sections are routinely “gamed” by trolls, many of whom pose as numerous different people in order to create a fake consensus, who attempt to debunk whatever information is being discussed, no matter how credible and well documented. We have seen this on our own websites for years and although some of those individuals were acting of their own accord, a significant number appeared to be working in shifts, routinely posting the same talking points over and over again. It is a firmly established fact that the military-industrial complex which also owns the corporate media networks in the United States has numerous programs aimed at infiltrating prominent Internet sites and spreading propaganda to counter the truth about the misdeeds of the government and the occupations of Iraq and Afghanistan. In 2006 CENTCOM, the United States Central Command, announced that a team of employees would be hired to engage “bloggers who are posting inaccurate or untrue information, as well as bloggers who are posting incomplete information,” about the so-called war on terror. In May 2008, it was revealed that the Pentagon was expanding “Information Operations” on the Internet by setting up fake foreign news websites, designed to look like independent media sources but in reality carrying direct military propaganda. Countries like Israel have also admitted to creating an army of online trolls whose job it is to infiltrate anti-war websites and act as apologists for the Zionist state’s war crimes. In January last year, the US Air Force announced a “counter-blog” response plan aimed at fielding and reacting to material from bloggers who have “negative opinions about the US government and the Air Force.” The plan, created by the public affairs arm of the Air Force, includes a detailed twelve-point “counter blogging” flow-chart that dictates how officers should tackle what are described as “trolls,” “ragers,” and “misguided” online writers. New revelations highlight the fact that the Obama administration is deliberately targeting “conspiracy groups” as part of a Cointelpro style effort to silence what have become the government’s most vociferous and influential critics. In a 2008 article published in the Journal of Political Philosophy, Obama information czar Cass Sunstein outlined a plan for the government to stealthily infiltrate groups that pose alternative theories on historical events via “chat rooms, online social networks, or even real-space groups and attempt to undermine” those groups. The aim of the program would be to “(break) up the hard core of extremists who supply conspiracy theories,” wrote Sunstein, with particular reference to 9/11 truth organizations. Sunstein pointed out that simply having people in government refute conspiracy theories wouldn’t work because they are inherently untrustworthy, making it necessary to “Enlist nongovernmental officials in the effort to rebut the theories. It might ensure that credible independent experts offer the rebuttal, rather than government officials themselves. There is a tradeoff between credibility and control, however. The price of credibility is that government cannot be seen to control the independent experts,” he wrote. “Put into English, what Sunstein is proposing is government infiltration of groups opposing prevailing policy,” writes Marc Estrin. “It’s easy to destroy groups with “cognitive diversity.” You just take up meeting time with arguments to the point where people don’t come back. You make protest signs which alienate 90% of colleagues. You demand revolutionary violence from pacifist groups.” This is what Sunstein is advocating when he writes of the need to infiltrate conspiracy groups and sow seeds of distrust amongst members in order to stifle the number of new recruits. This is classic “provocateur” style infiltration that came to the fore during the Cointelpro years, an FBI program from 1956-1971 that was focused around disrupting, marginalizing and neutralizing political dissidents. “Sunstein argued that “government might undertake (legal) tactics for breaking up the tight cognitive clusters of extremist theories.” He suggested that “government agents (and their allies) might enter chat rooms, online social networks, or even real-space groups and attempt to undermine percolating conspiracy theories by raising doubts about their factual premises, causal logic or implications for political action,” reports Raw Story. Sunstein has also called for making websites liable for comments posted in response to articles. His book, On Rumors: How Falsehoods Spread, Why We Believe Them, What Can Be Done, was criticized by some as “a blueprint for online censorship.” The Infowars office has been visited on numerous occasions by the FBI as a result of people posting violent comments in response to articles. Since the government now employs people to post such comments in an attempt to undermine conspiracy websites, if a law were passed making websites accountable, Sunstein’s program would allow the government to obliterate such sites from the web merely by having their own hired goons post threats against public figures. The fact that the government is being forced to hire armies of trolls in an effort to silence the truth shows how worried they are about the effect we are having in waking up millions of people to their tyranny. INFILTRATION http://rawstory.com/2010/01/obama-staffer-infiltration-911-groups/ In a 2008 academic paper, President Barack Obama's appointee to head the Office of Information and Regulatory Affairs advocated "cognitive infiltration" of groups that advocate "conspiracy theories" like the ones surrounding 9/11. Cass Sunstein, a Harvard law professor, co-wrote an academic article entitled "Conspiracy Theories: Causes and Cures," in which he argued that the government should stealthily infiltrate groups that pose alternative theories on historical events via "chat rooms, online social networks, or even real-space groups and attempt to undermine" those groups. As head of the Office of Information and Regulatory Affairs, Sunstein is in charge of "overseeing policies relating to privacy, information quality, and statistical programs." They claim that conspiracy theories typically stem not from irrationality or mental illness of any kind but from a 'crippled epistemology, ' in the form of a sharply limited number of (relevant) informational sources." By "crippled epistemology" Sunstein means that people who believe in conspiracy theories have a limited number of sources of information that they trust. Therefore, Sunstein argued in the article, it would not work to simply refute the conspiracy theories in public -- the very sources that conspiracy theorists believe would have to be infiltrated. Sunstein, whose article focuses largely on the 9/11 conspiracy theories, suggests that the government "enlist nongovernmental officials in the effort to rebut the theories. It might ensure that credible independent experts offer the rebuttal, rather than government officials themselves. There is a tradeoff between credibility and control, however. The price of credibility is that government cannot be seen to control the independent experts." Download a PDF of the article here <http://papers. ssrn.com/ sol3/papers. cfm?abstract_ id=1084585> . Sunstein argued that "government might undertake (legal) tactics for breaking up the tight cognitive clusters of extremist theories." He suggested that "government agents (and their allies) might enter chat rooms, online social networks, or even real-space groups and attempt to undermine percolating conspiracy theories by raising doubts about their factual premises, causal logic or implications for political action." "We expect such tactics from undercover cops, or FBI," Estrin writes <http://theragblog. blogspot. com/2010/ 01/got-fascism- obama-advisor- promotes. html> at the Rag Blog, expressing surprise that "a high-level presidential advisor" would support such a strategy. Estrin notes that Sunstein advocates in his article for the infiltration of "extremist" groups so that it undermines the groups' confidence to the extent that "new recruits will be suspect and participants in the group’s virtual networks will doubt each other’s bona fides." Sunstein has been the target of numerous "conspiracy theories" himself, mostly from the right wing political echo chamber, with conservative talking heads claiming he favors enacting "a second Bill of Rights <http://mediamatters .org/research/ 201001110052> " that would do away<http://stopsunstein .com/> with the Second Amendment. Sunstein's recent book, On Rumors: How Falsehoods Spread, Why We Believe Them, What Can Be Done, was criticized by some on the right as "a blueprint for online censorship." Sunstein "wants to hold blogs and web hosting services accountable for the remarks of commenters on websites while altering libel laws to make it easier to sue for spreading 'rumors,'" wrote Ed Lasky <http://www.american thinker.com/ blog/2009/ 07/cass_sunstein s_despicable_ idea.html> at American Thinker.
Prison Planet.com
Thursday, January 14, 2010